I'm seeing a strange anomaly in some systems I support.
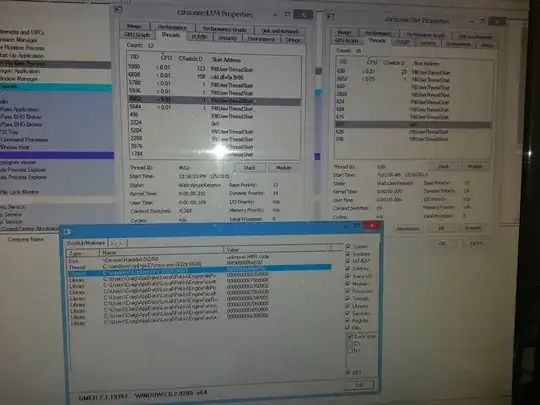
GMER flags the cdd.dll thread in csrss.exe, and when I run Process Explorer with Elevated Admin rights, I am:
- unable to view any loaded DLLs in either csrss.exe process
- unable to view actual thread start addresses (instead of winsrv.DLL and CSRSRV.dll, I see either 0x0 or !RtlUserThreadStart
- unable to view any csrss.exe thread's stack
- unable to suspend or kill any thread in csrss.exe
- Strings in memory show "Error opening process"
According to the 6th Edition of Windows Internals, this is what one would see in Process Explorer when trying to view the threads of "protected process"...
...Process Explorer is unable to show the Win32 thread start address and instead displays the standard thread start wrapper inside Ntdll.dll. If you try clicking the Stack button, you'll get an error, because Process Explorer needs to read the virtual memory inside the protected process, which it can't do.
However, csrss.exe is NOT a protected process. Also, even if were, one can normally still suspend "protected processes", which is not possible in this case.
For reference, this is what it normally looks like in Process Explorer...taken from a freshly installed system.
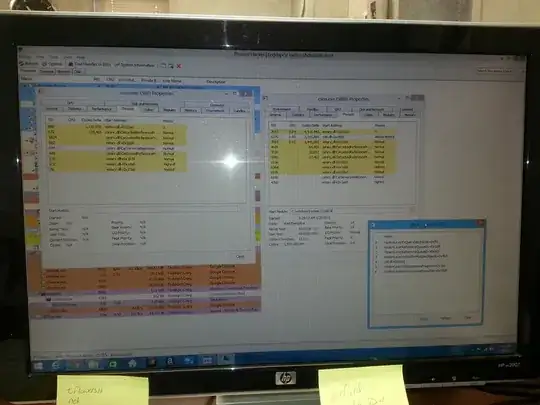
No other tool I've ran detects anything malicious. However, Process Hacker is able to access the threads, and they look like what I would expect to see...
2 things I know, I think:
- This is abnormal behavior (most other systems I look at give Elevated Admin full access to csrss.exe threads, strings, etc.)
- This seems consistent with rootkit-like hiding behavior. According to this quote from the book "Malware Analyst's Cookbook":
If a rootkit finds a reliable way to hide or prevent access to csrss.exe without causing system instability, then that could cause an issue. In fact, the author of CsrWalker found that some hackers tried to prevent CsrWalker from working by hooking ZwOpenProcess and preventing the detection tool from reading the memory of csrss.exe.
Can anyone explain why an Admin running PE with elevated rights would see these anomalies, other than an unknown rootkit?