I've registred a SPN, now I want to try to get a ticket for it. I know there is linux kvno to do that is there an analog on windows?
4 Answers
In Linux you can use "kinit" to verify specified SPN. This tool creates a Kerberos AS-ticket and stores it in a cache. Because of security reasons, this cache is meant to be used by operating system components.
To have kinit in Windows I install latest Java JDK (http://www.oracle.com/technetwork/java/javase/downloads/index.html).
Syntax: kinit <SPN>. Application will ask you for the password. If you'd enter correct password, you'll have AS-ticket created and stored in Kerberos cache.
Then you may list content of Kerberos cache, using klist -c.
- 103
- 4
- 236
- 2
- 8
-
The source code for the Java `kinit` implementation is currently available here https://github.com/frohoff/jdk8u-dev-jdk/blob/master/src/windows/classes/sun/security/krb5/internal/tools/Kinit.java#L142 – ATOMP Jan 22 '21 at 17:51
-
kinit gets you a TGT instead of a service ticket. See @markus-kuhn's answer about "klist get" instead. – Eric Jun 08 '22 at 13:46
The windows equivalent to kinit for realm CORP.CONTOSO.COM is:
- Add the SAMAccountName as the user credentials for the realm in
Control Panel > User Accounts > Credential Manager > Windows Credentials
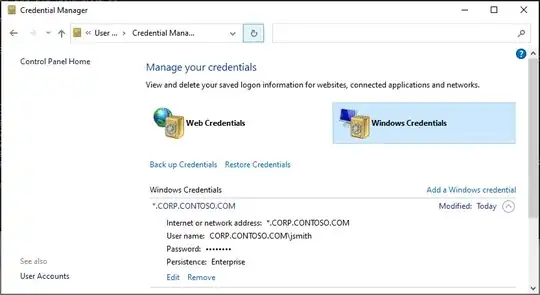
Note 1: you must use the realm exactly. You cannot use the domain name or a UPN. E.g.:CORP.CONTOSO.COM\jsmithis fine, butCORP\jsmithand[email protected]will fail.
Note 2: This can alternately be done usingcmdkey /add:*.CORP.CONTOSO.COM /user:CORP.CONTOSO.COM\jsmith /pass
Note 3: These saved credentials are retained indefinitely in your roaming profile. Remove them afterwards if this is not desired. - Make the connection to the service (using ssh, CIFS, RDP/TERMSERV, etc…) and verify a service ticket was created using
klist. Alternately you can request a ticket explicitly usingklist get SPN(e.g.: for CIFS on dc1 withklist get cifs/dc1.CORP.CONTOSO.COM)
Alternately, you can use runas for temporary connections (avoiding saved creds in credential manager):
- Use
runas /netonly /user:CORP.CONTOSO.COM\jsmith cmdto startcmdwith a new access token - Make the connection to the service and verify kerberos auth succeeded with
klist
Related:
- 1,143
- 1
- 9
- 16
Kerberos tickets can be generated using ktpass aswell. On windows prompt (Assumed KDC is installed)
ktpass -out <file>.keytab -mapuser <username>@REALM-IN-CAPS -pass <of-user> -crypto all -ptype KRB5_NT_PRINCIPAL -princ spn-of-user@REALM-IN-CAPS
This will generate *.keytab in current working directory.
- 153,128
- 77
- 353
- 394
- 11
- 1
-
4`ktpass` is used to create keytab files (which contain pairs of SPNs and password hashes). That is not the same thing as a Kerberos ticket. – jschreiner Oct 11 '19 at 13:55