Besides the frame busting trick, I would suggest getting the IPs of the servers that serve the framed pages and block them. If you are using China Telecom like me, they don't always frame the pages and, when they do so, a simple reload will give you the un-framed page. I guess they cannot frame everything since hijacking millions of connections per minute would bring down their resources quickly.
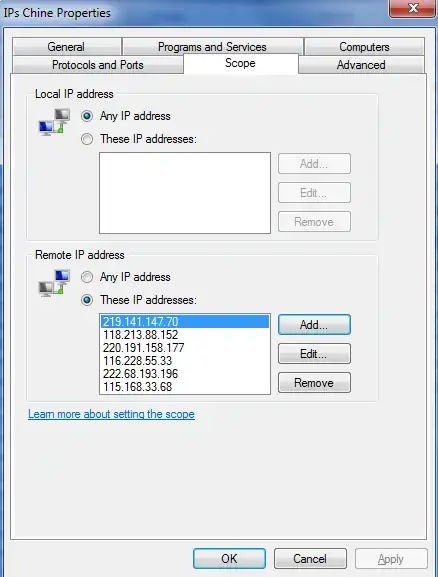
So what I ended up doing is to block all these IPs so I get a clean connection error when they try to mess with the current request. Then I know I can reload to get the real page. An added advantage of this method is that you don't send these servers any information, while for the frame-busting trick, the request still goes there (and given the crap they send back, I wouldn't trust them with the sensitive info that might end up in their logs).
For information here the IPs I've currently collected and blocked: