I have a client certificate for Satrtcom. I'm trying to authenticate to their service, but I'm receiving a "Secure Connection Failed" error with error code ssl_error_handshake_failure_alert:
The Startcom certificate and private key are present in Keychain:

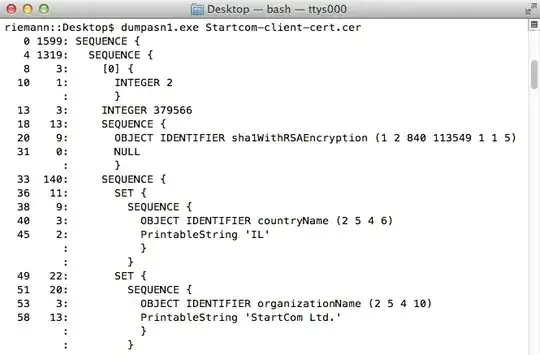
The certificate sumps correctly using Peter Gutmann's dumpasn1:
And it dumps correctly using OpenSSL's x509 utility:
The Keychain allows access to the certificate by Firefox (I just added it).
However, the issue persists. Tracing with Wireshark, I can see the client's Certificate message, but I don't see my client certificate in it (notice Certificate Lengths is 0):
Does anyone know what knobs to turn to have Firefox send the certificate rather than an empty Certificate message?
UPDATE: from https://stackoverflow.com/questions/1331722/client-certificates-and-firefox, the certificate is not listed under "My Certificates". This is expected since I want Firefox to use the certificate and private key in the Keychain.
So the question becomes, how do I instruct Firefox to use the certificate and private key in the Keychain?
UPDATE: This looks like a Firefox on Mac OS X bug (there was another similar bug in Firefox's bug reporter). See Cannot use Client Certificate stored in Mac OS X Keychain (or cannot figure out how to do it).
Any workarounds for this issue are welcomed.